Business Proposal to Porivde Cyber Security Protection
| ✅ Paper Type: Free Essay | ✅ Subject: Security |
| ✅ Wordcount: 4516 words | ✅ Published: 18 May 2020 |
Table of Contents
Option 2 Build a Cyber security team
Option 3 Outsourcing to an External company
5. Setting up an internal security team
Chief Security Officer /IT Manager
Security training and awareness
6. Hardware and software requirements
1. Executive Summary
This business proposal looks at options of providing cyber security protection to our business. It details what we need to put into place to develop a cyber security team to stop our business being affected by cyber-attacks. The proposal looks at options of doing nothing and staying as we are working currently, creating an in-house security team or outsourcing to experts in this field and reason for choosing preferred option.
Market research showing current trends, and lessons learnt from similar companies to ours that have been involved in cyber-attacks has been done.
Costing to put the proposal into place is provided, and also details of setting up an internal security team, with roles and responsibilities clearly defined for each team.
A detailed project plan showing steps and timescales required to implement have also been included
2. Background
ABC Insurance Company Limited was formed in July 2003. We are a English registered company and have a branch offices in majority of UK cities and branching out worldwide. We are authorised by the Financial Services Commission in England.
We are the Underwriters for a variety of personal lines policies for other companies including Asian based Insurance venture capital companies and Mobile Insurance Services Limited. All our transactions are on-line with Data Services and Infrastructure based in our head office. We employ over 1000 staff and deal with over 10000 customer accounts. We hold a lot of personal information in addition to the policy details.
More and more companies are being subject to cyber-attacks, where they are being held to ransom or hacked. If this is not dealt with it could lead to our business closing down, losing valuable customers, damaging company reputation.
One example of this is the holiday insurance company Staysure. Staysure Ltd are an online holiday insurance and financial services company in the UK and Europe. They were fined £175,000 after hackers were able to access customer records. The hackers were able to get access to customer’s personal details i.e. credit card numbers, medical records and CVV numbers which should not be stored. (Deng, 2015)
Another example is Marriot international. Marriot International is an American hospitality company. In November 2018 Marriot International was attacked by hackers. The attackers managed to steal 500 million data from customers. For some only name and contact information were stolen, but for others passport numbers, credit card numbers and expiry dates were also stolen. (Armerding, 2018) and there are many more companies that have been left vulnerable to these cyber-attacks.
Our company is at risk to cyber threat as well as Insider threat. Lord (2018) mentions an insider threat is a security threat that originates within the company, this is often an employee of the company.
An insider threat can also be described as threat that cannot be prevented by traditional security measures which focuses on preventing unauthorised attacks from the outside or defence against traditional hacking methods. (Lord, 2018)
An insider threat can be intentional or unintentional, it can also be someone who gains access to the system using an existing employees credentials.
Team ObserveIT (2018) also mentions a unintentional insider threat is can occur if someone has misplaced their device or accidentally clicks on a phishing link.
PwC’s Global State of Information Security Survey 2018 states that “87 percent of global CEOs say they are investing in cyber security to build trust with customers.” This has prompted our CEO to commission a Business Proposal for Options to address these threats.
Our company is very similar to Staysure, i.e we are an online insurance company that deals with sensitive information such as customer’s names, date of birth, Phone numbers, Emails, Address, Payment card numbers and expiry dates. Currently there is no one monitoring the system to ensure that the hackers cannot attack the system. As a financial company security should be our main priority so that we avoid being in the similar position to Staysure and Marriot.
3. Proposal
The proposal is for our company to set up an internal security team. This team will be beneficial to the company as they will be able to perform regular audits, patches and various other system checks to ensure it is secure. The Cyber Security team would also deal with incidents if the system were to be attacked and be at the forefront of technology, ensuring our company was prepared for any possible attack in the future.
To properly understand the Risk to our organisation we conducted an analysis of Impact of non-compliance against Security standards, that is identified the various compliance standards and issues like GDPR etc.
Being able to guarantee that the data of our clients are protected, that’s priceless. We can even market this into a unique selling proposition and really get the word out that consumers can trust you with their data. A big advantage of choosing for this strategy is that it’s still early in the game: There aren’t a lot of competitors who focus on guaranteeing the safety of their customers’ data. This can also help to attract investors for your company.
I undertook a structured approach to requirements of the Business Proposal on behalf of the company and identified 4 strategic options, each of these were analysed, and based on the analysis a recommendation has been presented to the CEO. The analyses were as follows:
Option 1 Do nothing
NOT having Cyber security will cost our organisation a lot more than doing nothing!. When a safety breach occurs, our company will be forced to invest in a safety net anyway. Establishing a cyber-security department or outsourcing is a solid investment that not only will protect our firm from paying high fines, but it will also save our company from damaging its reputation and losing clients.
If an attack on the company is successful it can cause major damage to the business. The impact of having a security breach can result in financial loss, reputational damage and legal cases.
If a hacker is able to attack our system they could gain access to sensitive information such as our Customers bank account number, expiry dates, Customer contact information or our Corporate information that could help competitors get ahead of us, this can result in a financial loss for both the company and the customers. (nibusinessinfo.co.uk, nd)
Cyber-attacks can damage the businesses reputation and can lead to lack of trust in customer and reduce profits. (nibusinessinfo.co.uk, nd)
As the company holds personal and sensitive information the company can be held liable if an unwanted third party is able to get access to the information. This would be a breach of the data protection and privacy law and can result in a fine. (nibusinessinfo.co.uk, nd)
A security incident can delay, disrupt or even shut down our business operations. For our insurance company that would mean that we suffer from sales losses, for a service sector like ours it is a barrier to provide good customer support
Being a victim of cyber security breaches can subject us to ongoing regulatory reviews forcing our business to comply with several audits, additional tax compliances, incident response plans, limits on access privileges and more. And it doesn’t end there, cyber security regulations come with enforced penalties with short deadlines. Penalties vary depending on the industry, and the incident
Option 2 Build a Cyber security team
The advantages of having an in house team are that we keep control of all our data and do not off load the risk to an external company. We can monitor what our staff are doing and prioritise tasks. We already have an internal IT team, with highly skilled engineers, these staff have been working with the company for a long time and can be trusted to deal with sensitive information. They understand the process, procedures, the hardware and software we are currently using.
Our business is unique internal security team will provide the flexibility to tailor our applications to fit the business needs and budget. Hours and levels of service can also be tailored. Internal investment will allow us the flexibility to pick best of breed tools rather than contract to individual branded tools allowing for inflexibility in the future.
The employees already have IT based knowledge and may only need training in cyber security and how to prevent cyber-attacks. We will need to invest in additionaltraining as appropriate, the cost to train employees internally will be a lot cheaper.. Our operations are already mapped to a security framework; we have the knowledge to strategically plan document and implement the security processes.
Staff will be motived and keen to stay with the business, knowing they are getting training and working with the latest technologies. Our Staff will need to learn the difference between the GDPR, the DPA (Data Protection Act) 2018 and PECR (Privacy and Electronic Communications Regulations).
The disadvantages are If external staff are required to be hired due to us not having the skilled staff, this could be difficult or expensive as there is a security skills shortage, these experts can be difficult to find and expensive to hire.
To stay current in the ever-changing world of technology, means having to constantly invest in support training for our IT staff. When Time to business value is critical we may not have the relevant tools and staff trained in time.
This level of maintenance can also prove to be a costly strain on the business.
As the administrator of the system will have full control of the company network and can see all data and information across the organisation, strict security controls will have to be put in place to prevent security breaches.
Need enough resource providing holiday or sick cover. Out of working hours may require putting in shift work that staff may not accept.
Option 3 Outsourcing to an External company
The advantages of outsourcing to an external company is that we will have experts who are already trained and have an understanding of how cyber criminals work and the techniques they use. (redscan.com, 2017)
If we outsource an expert will be able to identify and respond to an incident straight away as they will be monitoring systems 24/7. (redscan.com, 2017)
To protect our business from cyber-attacks we may need to purchase advanced technology to detect vulnerabilities. It will be difficult to know what technology to purchase, by outsourcing we will have experts that know what the best technology to purchase is and how it can help us in the long run. (redscan.com, 2017)
Another advantage of outsourcing is that experts will know how to test the defences of the company to identify gaps in the system that were previously unknown and provide advice on the action that need to be taken to fix the issues. (redscan.com, 2017)
The disadvantages to outsourcing is that it can be difficult to trust another company with our intellectual property and sensitive information. This can be a huge risk as there is no way of knowing what they will do with that information. Service Level Agreements (SLA’s) can be put into place that prevents them selling any data to competitors. (Riggins, 2017).
Outsourcing to an external company means that we will have to agree to the terms they propose. This means that if one the outsourced staff decided to use a different software or hardware component on the computer systems, this will result in a breach of contract with the existing security provider.. (Riggins, 2017).
Cost of customisation of our applications to meet with the interfaces of outsources cyber security systems maybe very expensive, as any change in applications may result in new interfaces being applied.
OPTION 4 Multi-facet Approach
There is an increased recognition for a multi-faceted approach to cyber security. As threats become increasingly more complex, so must our approach to tackling them.
Collaboration and flexibility is key in this respect. In order to be truly effective in identifying and responding to threats, businesses need to be prepared to welcome new technologies and tactics that will allow them to address their needs. True value in cyber security comes from tuning the solution to the environment. This can prove time consuming and difficult, but if we see the industry continue on its current trajectory, it’s likely that we’ll see an emergence of new cyber security strategies that combine the flexibility and all-purpose approach of external providers with the control of internal resource
The Managed Security Services Provider must be able to share information between team members and also prepare information for you, as the client, to approve. Internal programs are not likely to be documented nearly as thoroughly, which often means if a key team member were to leave, the result would be a security program that would take several steps backward. With the volume of opportunities available to cyber security professionals and the generational comfort with millennial to frequently switching organizations, the lack of documentation can result in great difficulty in maturing a program.
Option Analysis
Looking at these options 1 is too high a risk for our company and should be avoided, option 4 is preferred as it is least expensive and keeps our staff motivated and easy to retain. Option 3 is more expensive and we may lose control of our systems to 3rd parties.
4. Risk assessment
 This section will focus on the probability of risk and impact. This will be determined using a scale factor of 1 to 5 and is measured from very high to low. This can be seen in Table This Table will also be used to assess the level of risk in table 2.
This section will focus on the probability of risk and impact. This will be determined using a scale factor of 1 to 5 and is measured from very high to low. This can be seen in Table This Table will also be used to assess the level of risk in table 2.
Table 1 – Risk & impact table
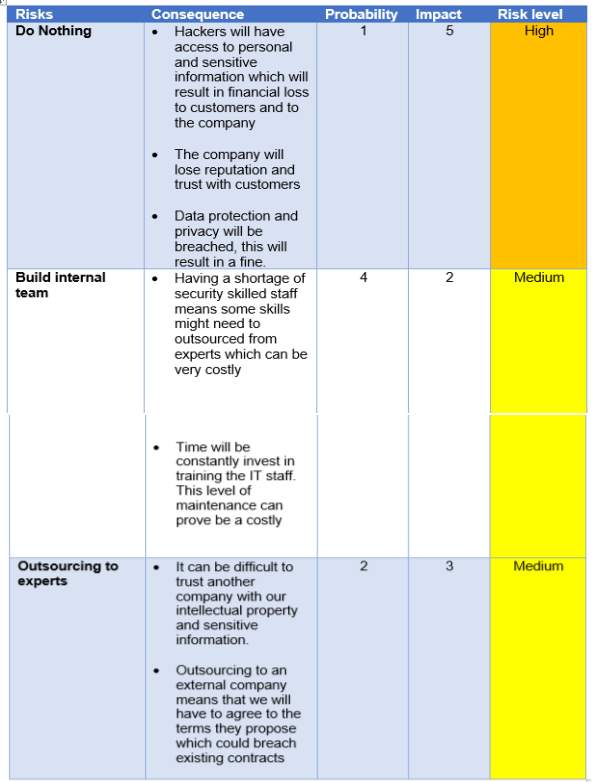
Table 2 – Risk assessment
5. Market Research
Bert Rankin (2019) states nearly 70% of businesses had experienced some form of cybersecurity attack, and over half of them had experienced a data breach. Rankin also mentions data breaches and network security threats are expected to rise in 2019.
A recent government survey estimated that the average cost of a small business’s worst cyber-attack is between £65,000 and £115,000. However, according to specialist business insurance broker PolicyBee, 74 per cent of small businesses haven’t put any money aside to deal with an attack. (bbc.co.uk, 2019)
A recent study from computer and network security company eSentire has found that cyber-attacks in the UK spiked by over the course of last year. According to the study, Britain was stung by 140% more cyber-attacks than the previous year (Consultancy.uk,2019)
Hydro a global aluminium producer was hit by a Ransomware attack. Hackers were able to gain access to the computer system, once they were inside the stystem they were able to discover a lot more weakness in their system. Approximately 22,000 computers were hit across several different site. (bbc.co.uk, 2018)
Murray Goldstein (n,d) Mentions four ways small businesses can protect themselves from cyber-attacks. (seen in appendix 2)
The best way to protect against the attack is by having a Cyber security team. The team will get involved in staff training, system/network audits, incident response management and software installations. (Techworld Staff, 2019)
1. Setting up an internal security team
Listed below are the roles and responsibilities of each member.
Roles and Responsibilities
Chief Security Officer /IT Manager
- Assemble the right management team and delegates certain responsibilities to them for the benefit of the business. (profitableventure.com, n,d)
Security/network analyst
- Responsible for creating system defence against unauthorized access or modifications from external threats
- Configure the right security tools such as anti-virus software, firewalls and patch management systems on behalf of the firm
- Performs on behalf of the firm, vulnerability and networking scanning assessments (profitableventure.com, n,d)
The incident response team
- When an incident arises the incident response manager will oversee the action made during the detection, analysis, and the eradication of the incident.
Audit Management Specialists:
- Audit user activity ensuring company polices are adhered to.
- The audit team will ensure the current security policies are in place and ensure the company isn’t breaking any laws such as (GDPR) General Data Protection Regulation 2018 – This law ensures:
- “The ‘right to access’ – a right of access to all their personal data, currently known as a subject access request (SAR)”.
- “The ‘right to rectification’ if data is wrong”.
- “The ‘right to be forgotten’, or have their personal data erased”.
- “The ‘right to restriction’ of processing upon request under certain conditions”.
- “The ‘right to data portability’, i.e. get an electronic copy of all their personal data, or request it is transmitted from one data controller to another”.
- “The ‘right to object to processing’”.
- “The right not to be subject to automated decision-making processing that produces legal effects or significant affects”. (Gov.uk, 2018)
An article by ITgovernance (2019) mentions that by not obeying the GDPR law can result in a fine that result up to 4% of annual global turnover or €20 million – whichever is greater (Itgovernance.co.uk, n,d).
- The audit team will vet all employees
(A list of security polices can be seen in appendix 1)
Change control
The change team will have security, technical and end users experts on the board to review the change. The change request will have details of the change, testing pre and post the change, the risk, mitigations and roll back plan. The risk and technical change need to be reviewed by the experts prior to approval. All changes will be documented and audit trail maintained. All users affected by the change need to be notified in advance. Emergency changes will be given the highest priority.
Security training and awareness
As a financial company it is important that any sensitive information is stored securely and encrypted. Training of all staff members is important not just the security team. All staff will be trained on our security policies and procedures, how to create strong passwords and distinguish between a genuine email and phishing emails. They will also be trained how to report any phishing received.
Training of cyber security team to ensure their skills and knowledge of current trends in cyber security are further developed i.e. the potential vulnerabilities that can impact the business such as Hackings, phishing, Social engineering attacks and Malware threats. It is important that the cyber security team is well trained to deal with any potential cyber threats.
2. Hardware and software requirements
To ensure our systems are protected from potential threats the cyber security team will trained to use the latest state of the art technology.
A recent article from globalsign (2018) mentions 4 cyber security tools that are essential to small business are:
- Firewall
Hackers have become more skilled have learned how to create programs that trick firewalls into believing that they are a trusted source. For this reason, it is important that the company ensure that our firewalls are hardened.
- Anti-virus
It is crucial our company has an Antivirus software installed and configured properly. The antivirus software will alert virus and malware infections and provide additional services such as scanning emails to ensure they are free from malicious attachments or web links
- Penetration testing
Penetration testing is the best way to test our business’ security. The cyber security team will use the same techniques used by cyber criminals to check potential vulnerabilities in the system. A pen test attempts to simulate the kind of attack a business might face from criminal hackers, including everything from password cracking and code injection to phishing.
3. Financial plans
Estimated Outsourcing Costs~ 100k pa
Key activities provided
- Project management:
- Out of hour’s support
-
Continuous Assessment:
- Security Audits
- Penetration tests
- Vulnerability testing
- Patching /Change control
- Compliance
- Training
Estimates for creating In house costs 45k pa.
Chief Security Officer – 70k (Role will be done by our existing IT manager)
2X Network Engineers 50k (Existing engineers will be up skilled)
1X Auditor (additional staff will be recruited) £25k pa
1X Legal (Existing legal team member will be used)
1x Trainer (Training will need to be done by external teams) 10k
Out of hours support costs: 20k
Hardware and Software : 25k
Appendices
Appendix 1 – Policies
Protect sensitive data
All sensitive data stored and handled by the Company and its employees must be securely protected against unauthorised use at all times. Any sensitive customer data that is no longer required must be destroyed in a secure and recoverable manner.
Physical Security
In order to prevent unauthorised individuals accessing or obtaining sensitive data, they must be physically restricted.
Network security
The network security team will ensure: Firewalls are implemented as required by network standards. i.e to separate the internal company network, from all the internet connections and any demilitarised zone.
Router configurations restrict connections between untrusted networks and any systems in the secure data environment. All traffic has to traverse through a firewall.
Anti-virus policy
The network security team will ensure the latest anti-virus software is ran periodically on all systems, and all removable media should also be scanned for viruses before being used.
Patch Management Policy
The network team will ensure all systems have the latest security patches installed, within one month of being released by the vendor. Where possible these should happen as an automatic update. Any exceptions have to be documented.
Audit Policy
The audit team will ensure all logs generated by the company, i.e. security scan logs, patching logs, customer calls logged, network logs, database audit logs are saved for three months. The audit team need to review these logs daily using network monitoring tools and take action if issues, are identified. This also allows the company to investigate security breaches and ensure compliance with legal or contractual requirements.
Incident Response
The incident response team will be logged any incident for audit purposes. It is crucial that the company investigates incidents as soon as they happen, to keep the company systems safe
Appendix 2 – How to prevent a cyber attack
- Understand Emerging Trends and Evolving Risks
The best way to prevent a cyber-attack is to have an understanding of the potential vulnerbalities that can impact a business.
- Hacking – Hacking is one of the most common cyber attacks i.e. Email or system hacks. This usually occurs when a cyber-criminal is able to gain unauthorised access to someone’s email or system. When they are able to do this they can manipulate the data for their own benefit
- Phishing – A phishing attack is very common in small business. This type of attack occurs through a fraudulent website that appears to be legitimate. The hacker is able to collect personal information from this such as: passwords and credit card information.
- Social Engineering – A social engineering attack is done through the means of social interaction. Once trust is built up with an individual they attacker is able to gather enough information on the person to steal information from them
- Malware Threats – Malware is software created by hackers that can be sent to devices or online platforms in order to get access to your personal information. It cannot damage the physical hardware of your systems and equipment, but it can do a lot of harm to the data and software within them.
(Goldstein, nd)
- Develop a Security Policy
To protect against cyber-attacks it is crucial that security protocols are defined. These protocols should be part of the business strategy. The reason for this is more and more sensitive data is being stored digitally and it is important the security polices addresses standard practices such as audits and backups and newer security concerns such as The internet of things and social media security.
- Keep Your Hardware, Software, and Security Safeguards Up-To-Date
To ensure there are no holes in the system anti-virus software and other security applications must be kept up to date. This will help to protect the company against new threats and make sure your infrastructure is secure. These precautions should include:
- “Using a Firewall for your internet connection”
- “Installing, using, and regularly updating anti-malware, anti-virus, and anti-spyware software on every computer used in your business”
- “Downloading and installing software updates as they become available”
- “Monitoring your systems continuously to detect potential problems”
- Educate Your Employees
One of the biggest problems in business’ is that a lot of employees are unaware of the risk and implications of being attacked by a cyber criminal. Staff should be trained in cyber security and should be able to spot warnings signs of a potential cyber attack.
References & bibliography
- DENG, C. (2015) Online travel insurer Staysure.co.uk fined £175,000 for data lapse | marketinglaw. [Online] Available from: https://marketinglaw.osborneclarke.com/data-and-privacy/online-travel-insurer-staysure-co-uk-fined-175000-for-data-lapse/ [Accessed 19/7/2019]
- ARMERDING, T. (2019) The 18 biggest data breaches of the 21st century. [Online] Available from: https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html [Accessed 25/7/2019]
- nibusinessinfo.co.uk (n,d) Impact of cyber attack on your business. [Online] Available from: https://www.nibusinessinfo.co.uk/content/impact-cyber-attack-your-business [Accessed 25/7/2019]
- CYBOAR.CO.UK. (2018) 3 advantages of outsourcing your Cyber security – Cyboar. [Online] Available from: https://cyboar.co.uk/3-advantages-of-outsourcing-your-cyber-security/ [Accessed 25/7/2019]
- COMTACT.CO.UK. (2017) Pros and cons of outsourcing your Cyber Security – In-house, MSSP, or Virtual SOC?. [Online] Available from: https://www.comtact.co.uk/blog/pros-and-cons-of-outsourcing-your-cyber-security-in-house-mssp-or-virtual-soc [Accessed 25/7/2019]
- MELNICK, J. (2018) Top 10 Most Common Types of Cyber Attacks. [Online] Available from: https://blog.netwrix.com/2018/05/15/top-10-most-common-types-of-cyber-attacks/ [Accessed 25/7/2019]
- RANKIN, B. (2019) Cybersecurity Statistics for 2019: The Chances Your Business Will Be Attacked. [Online] Available from: https://www.lastline.com/blog/cybersecurity-statistics-for-2019/ [Accessed 25/7/2019]
- BBC.CO.UK. (2019) Cyber-attacks on UK firms ‘jump’ in 2019. [Online] Available from: https://www.bbc.co.uk/news/business-48017943 [Accessed 25/7/2019]
- PROFITABLEVENTURE.COM. A Sample Cyber Security Business Plan Template | ProfitableVenture. [Online] Available from: https://www.profitableventure.com/cyber-security-business-plan/ [Accessed 25/7/2019]
- ITGOVERNANCE.CO.UK. General Data Protection Regulation | GDPR Overview | IT Governance UK. [Online] Available from: https://www.itgovernance.co.uk/data-protection-dpa-and-eu-data-protection-regulation [Accessed 25/7/2019]
- GOV.CO.UK. (2018)[Online] Available from: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/711097/guide-to-the-general-data-protection-regulation-gdpr-1-0.pdf [Accessed 25/7/2019]
- CONSULTANCY.UK. (2019) UK stung by 140% increase in cyber-attacks. [Online] Available from: https://www.consultancy.uk/news/21203/uk-stung-by-140-increase-in-cyber-attacks [Accessed 26/7/2019]
- GOLDSTEIN, M. 4 Ways Small Businesses Can Protect Themselves From Cyber Attacks. [Online] Available from: https://www.coxblue.com/4-ways-small-businesses-can-protect-themselves-from-cyber-attacks/ [Accessed 26/7/2019]
- JAHMEL. (2017) In-house IT Department vs outsourcing IT support? Pros and Cons. [Online] Available from: https://www.atg-it.co.uk/it-support/it-support-inhouse-vs-outsourcing/ [Accessed 26/7/2019]
- REDSCAN.COM. (2017) Key reasons to outsource your cyber security in 2018 | Redscan. [Online] Available from: https://www.redscan.com/news/key-reasons-outsource-cyber-security-2018/ [Accessed 29/7/2019]
- LORD, N. (2018) What is an Insider Threat? An Insider Threat Definition. [Online] Available from: https://digitalguardian.com/blog/what-insider-threat-insider-threat-definition [Accessed 26/7/2019]
- OBSERVEIT. (2018) The Primary Factors Motivating Insider Threats. [Online] Available from: https://www.observeit.com/blog/primary-factors-motivating-insider-threats/ [Accessed 26/7/2019]
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this essay and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



